Hackers unveil Ingenious Method to Bypass PIN Codes on Contactless Cards
The vulnerability was detected by the ETH Zurich team during their offensive research, which focused on uncovering details about this alarming discovery.
The ever-evolving world of hackers has struck again with a new discovery – the Man-In-The-Middle attack (MITM). This sophisticated hack allows cybercriminals to bypass PIN codes on Mastercard and Maestro contactless cards, paving the way for unauthorized payments on stolen cards without needing PIN verification.
The ingenious nature of hackers is both fascinating and alarming. Their technical expertise enables them to explore unconventional ways of breaking into computerized systems, making digitalization during the COVID crisis a breeding ground for increased cyberattacks worldwide.
The vulnerability was detected by the ETH Zurich team during their offensive research, which focused on uncovering details about this alarming discovery.
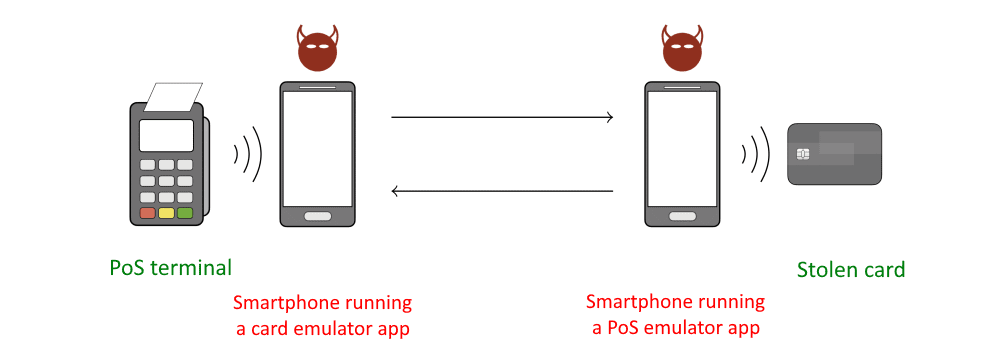
According to CyberSecurity News, the MITM attack requires a stolen card, two Android smartphones, and a custom Android application capable of manipulating transaction fields. The application is installed on both smartphones, which serve as emulators – one acting as a Point-of-Sale (PoS) terminal emulator, and the other as a card emulator.
The attack process begins when the stolen card is placed next to one smartphone, tricking the card into initiating a transaction and sharing its data. The fraudster uses the second smartphone to modify the transaction data and transfer it to a real PoS terminal inside the store.
From the perspective of the PoS terminal, it appears as if the customer is using a mobile payment app. However, the fraudster cleverly sends the modified transaction data from the stolen card.
While Mastercard has already addressed the issue with fixes, Visa has yet to resolve the vulnerability. This discovery raises concerns as future attacks may exploit new bugs in contactless payment protocols, making it essential for payment companies to remain vigilant.
The ETH Zurich team successfully tested the attack with various cards, including Visa Credit, Visa Debit, Visa Electron, and V Pay cards. Their findings highlight the urgency for payment companies to enhance security measures to thwart potential cyberattacks.
As this dangerous vulnerability remains unaddressed by Visa, it serves as a stark reminder that hackers continuously seek innovative ways to exploit weaknesses in digital systems, necessitating constant efforts to bolster cybersecurity defenses.